Network / PCI ASV Vulnerability Scanning
Cloud based PCI DSS approved network vulnerability scanning solutions to identify vulnerabilities in systems, network devices, applications and databases.
Advanced Network Vulnerability Scanning, with multi platform support
Highly scalable, Internal and External vulnerability scanning over the internet anytime from anywhere that identify over 60,000+ vulnerabilities across your entire network and supported cloud environments with constantly updated vulnerability database
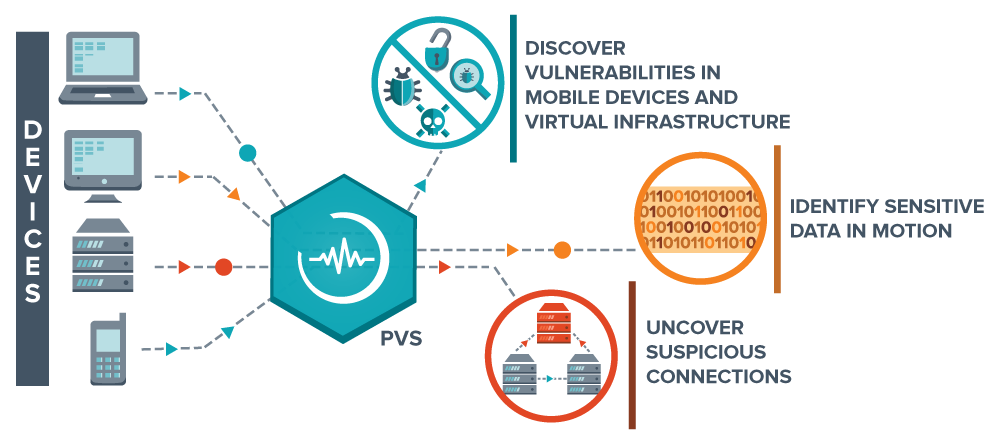
Quarterly Network vulnerability scanning for PCI DSS and other regulatory compliance
If you handle credit card data, you must be PCI compliant. To achieve and maintain PCI compliance, you must perform quarterly network vulnerability scanning. This is true for small and large companies alike. Failure to comply can result in large fines and losing the ability to process credit and debit card payments. Our security team specializes in helping SMBs and Mid-Markets understand and comply with the PCI Data Security Standard (DSS) regulations. We can help your organization reduce the risk of a security breach.
Many regulations, including PCI DSS, SOX, GLBA, HIPAAFFIEC, NERC CIP and FISMA, require organizations to test regularly for network security vulnerabilities. Our vulnerability scanning solution helps identifying and mitigating information security risk.

Research-driven Network Vulnerability Management
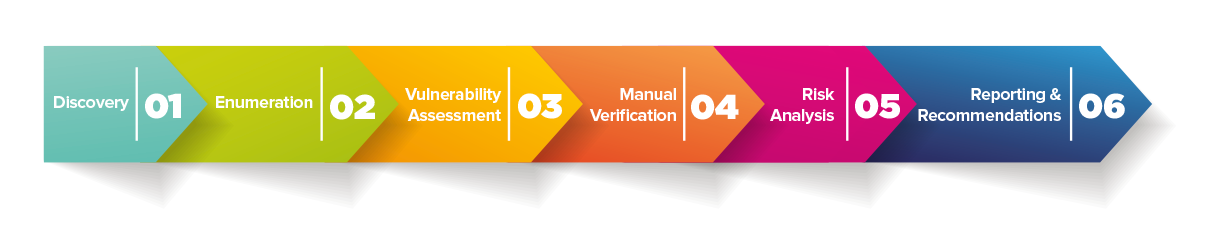
Easy ownership with a dedicated security expert team
The fully managed network vulnerability scanning service eliminates administrative overhead by providing complete operational support, from configuring the technology and scheduling scans to expert review of results, virtually eliminating false positives. By identifying the vulnerabilities in your environment and providing detailed analysis and remediation guidance, our network vulnerability scanning service helps you reduce your exposure, comply with regulations and safeguard your business.
Our experts apply their extensive knowledge and experience to verify and supplement the automated results with a manual review to eliminate false positives to ensure the results are of the highest fidelity to ensure reports produced contain rich, actionable intelligence, including detailed descriptions of network vulnerability, insight into the root cause, and available workarounds.

Comprehensive Reporting with remediation tracker support
Once you’ve performed vulnerability scanning of your assets for vulnerabilities, you need to develop a response plan that describes the vulnerabilities and their potential impact to your environment, and then decide which issues to remediate first. Doing this efficiently requires expert knowledge of not only the exploit methods but the affected systems as well.
Along with an array of remediation reports that provide security managers with a current snapshot of remediation status and progress, also Includes a highly automated, integrated remediation and trouble-ticketing workflow system.

Superior cybersecurity outcomes delivered as a service
Innovate with Confidence
The data shows why E Com Security Solutions is the right partner for your cyber security strategy.
Resources to help you drive cyber security and speed within your enterprise.
AI Impact Assessment Process
The nomenclature around AI impact assessments and its relationship to other evaluations of AI are unsettled. Some Organizations use “AI risk assessment” and “AI impact assessment” interchangeably, while others distinguish [...]
Vulnerability Response Playbook
One of the most straightforward and effective ways for an organization to prioritize vulnerability response and protect from being compromised is by focusing on vulnerabilities already being actively exploited in [...]
Insights on Vulnerability Management
Cyberattacks can cost millions to resolve and make headline news. The attack surfaces keep expanding as organizations connect assets, allow remote work, and promote virtual customer engagement. It's hard to [...]








