Firewall Security Assessment
Firewall Security Assessment helps you gain visibility on firewall configuration and access lists to secure, optimize, comply with regulations and manage to keep them secure from external threats.
Firewall Security Assessment with Well-defined, repeatable, and consistent methodology
Review the firewall device configuration, looking at industry best practices and hardening techniques, and interprets the rulesets by understanding the overall company architecture and will:
– Review the firewall configuration file for the identification and protection of all network segments.
– Review the processes and mechanisms for a security model that denies access by default.
– Review the implementation of open ports and services for all access points to the external presence.
– Review the documentation of those entries and the configuration of those ports and services.
– Identify the implementations of banners, access controls, and appropriate use policies.
– Review the implementation of processes for monitoring and logging access at access points to the network.
– Review controls for default accounts, passwords, and network management community strings.
– Review all ingress/egress points within the network.
– Identify best practices implementation and lack of hardening techniques.


Firewall Policy Compliance
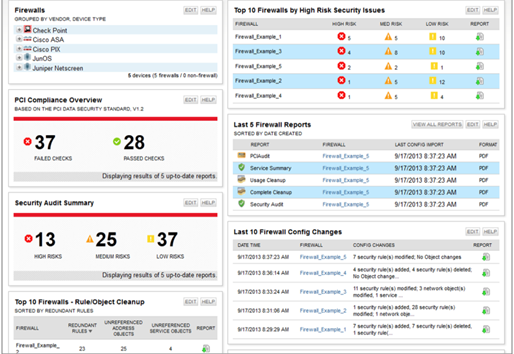
Firewall Security Assessment, ensures compliance with industry best practices, regulations and custom policies, including PCI DSS, SOX, ISO, NSA, NERC and FISMA with audit reports and compliance scorecards.
Scalable solution that lets you maintain continuous firewall compliance with automated, daily compliance checks for your entire enterprise.
Support a broad range of industry leading security solutions platforms, including:
Comprehensive Reporting with remediation tracker support
Firewall and Network device configuration assessment comprehensive reporting includes an Executive Summary, detailed vulnerability analysis, recommendations, and a prioritized action plan.
The Reporting addresses Regulatory requirements, including PCI DSS, SOX, ISO, NSA, NERC, and FISMA Compliance.

Strengthening your security operations posture
E Com Security Solutions’ risk management strategies assist organizations in identifying and prioritizing the remediation of vulnerabilities, as not all have equal impact. We adopt a systematic approach to identifying and mitigating risks due to vulnerabilities existing across different cloud platforms. Our services are designed to focus on the threats posed by privacy and security breaches in cyberspace and will comply with the required government legislation and regulations.
Superior cybersecurity outcomes delivered as a service
Innovate with Confidence
The data shows why E Com Security Solutions is the right partner for your cyber security strategy.
Resources to help you drive compliance and speed within your enterprise.
AI Impact Assessment Process
The nomenclature around AI impact assessments and its relationship to other evaluations of AI are unsettled. Some Organizations use “AI risk assessment” and “AI impact assessment” interchangeably, while others distinguish [...]
Vulnerability Response Playbook
One of the most straightforward and effective ways for an organization to prioritize vulnerability response and protect from being compromised is by focusing on vulnerabilities already being actively exploited in [...]
Insights on Vulnerability Management
Cyberattacks can cost millions to resolve and make headline news. The attack surfaces keep expanding as organizations connect assets, allow remote work, and promote virtual customer engagement. It's hard to [...]