What is two factor authentication?
You may have heard the term ‘two-factor’ or ‘multi-factor’ authentication. If you haven’t heard of these terms, chances are you’ve experienced this and not even known it. The interesting thing is that two factor authentication is one of the best ways to protect your accounts from being hacked. So what [...]
PwC Report Shows Cybercrime in the UK is Growing Rapidly
In the latest edition of their Global Economic Crime Survey, PricewaterhouseCoopers have announced a finding of a 20% increase in cybercrime, making it the fastest growing category of economic crime. The UK seems to be the most severely affected, with 55% of organisations being affected by some type of cybercrime, [...]
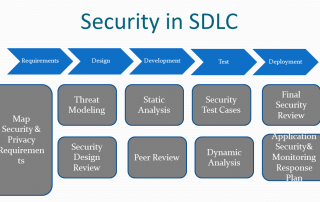
Six Best Practices for Security Testing in the SDLC
Even if an application has been built following security and defensive coding best practices, it will still require significant testing before it's ready for release. Whether this is routine testing for common vulnerabilities or security-focused penetration testing to pick up on the types of problems that often slip through the [...]
Mobile App Leads to Speeding Ticket Email Scam
A clever scam that involves a “free mobility or traffic app” is duping users by tracking their whereabouts and then sending a fake speeding ticket. Police in Pennsylvania detailed a scam that involves a mobile app, which may have been used to target people by sending them legitimate-looking speeding tickets [...]
Two thirds of companies fail to declare data breaches
A poll of 1000 Institute of Directors members in the UK has found that two thirds of the companies who fall victim to a data breach are failing to declare it publicly or report it to the police for fear of reputational damage. Also, only around half of companies have [...]