Web Services & Application Vulnerability Scanning
Web Services & Application Vulnerability Scanning provides a comprehensive evaluation of the security posture of an application or solution based on web services technologies like SOAP or REST.
Address security concerns with on demand web application vulnerability scanning
Assess modern and dynamic web apps and services
Web Services & Application Vulnerability Scanning is designed for modern web applications built on new technologies such as AJAX, SOAP/WSDL, SOAP/WCF, REST/WADL, XML, JSON, Java, .Net, PHP, Flash, Ruby on Rails, and Google Web Toolkit (GWT), as well as features such as shopping carts, forms, login pages, business workflows, and other types of dynamic content.
Advanced behavioural analysis helps identify even zero-day malware that eludes anti-virus and anti-spyware packages.


Comply with reporting requirements
Meet the industry best practices and legal and regulatory compliance regulations, including PCI DSS, FFIEC, SOX, HIPAA, GLBA, NERC CIP, and FISMA, which require organizations to perform Web Services & Application Vulnerability Scanning regularly and to demonstrate Compliance.
E Com Security Solutions’ expert team can support you in performing Web Services & Application Vulnerability Scanning to meet the respective compliance requirements and present you with compliance reporting, which also helps your team quickly see gaps in compliance and helps you mitigate information security risk.
Intelligent Scanning that identifies the real exploitable vulnerabilities
Technology that delivers the largest and most up-to-date knowledge base of vulnerability checks in the industry, covering OWASP Top 10, SANS Top 25, OSSTMM, and WASC to detect information security vulnerabilities across Web Services & Applications.
Intelligent custom attack Web Services & Application Vulnerability Scanning based on unique site structures, parameter names, and application architecture responses eliminates false negatives and host crashes.

Prioritize and track remediation with Interactive reports
Highly automated, integrated remediation and interactive, actionable reports that prioritize the highest risk and streamline remediation efforts by enabling users to get to and analyze the data that matters most quickly.
A wide array of remediation reports helps developers and business owners to identify the threat surface quickly and provides a current snapshot of remediation status and progress.
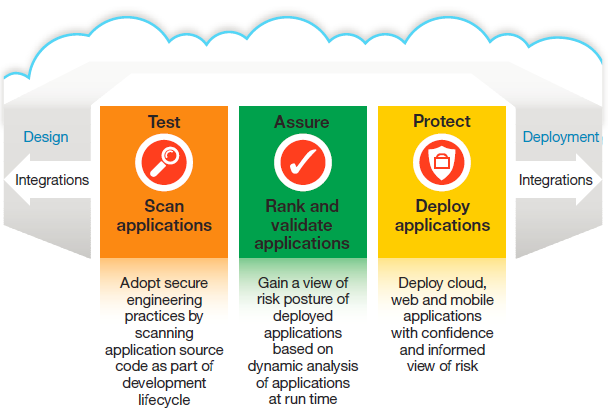
End-to-end application security, from design to deployment by integration application vulnerability scanning to cultivate a secure-by-design framework
Featured customers securing their Web Apps
Innovate with Confidence
The data shows why E Com Security Solutions is the right partner for your application security strategy.
Resources to help you drive security and speed within your enterprise.
Mitigating API Security Risks
Securing all your APIs is difficult. It’s even more complicated when your keys and tokens are exposed involuntarily in real-world settings, from APIs to frontends. Your organization is now prone [...]
Practical guide to API Security
APIs come in many flavours, including REST, SOAP, graphQL, gRPC, and WebSockets, and each has its use cases and common vulnerabilities. The issues covered in this guide can occur in [...]
Mitigating Application Security Threats
One of the key reasons for application vulnerabilities is a lack of secure design, development, implementation, and operations. Relying solely on post-development audits for security is inadequate. Instead, security must [...]